Between onboarding new hires and offboarding departing employees, manually managing Slack access can quickly turn into a security risk — or consume hours you don’t have. When you’re dealing with hundreds (or thousands) of users, every manual step adds up.
If you’ve ever chased down Slack accounts after someone left, or scrambled to add new users to the right workspaces and channels before day one, you’ve felt this pain firsthand. Many IT admins tell us the same thing: “We want to automate access control, starting with SSO and user deprovisioning.”
That’s what the Slack–Okta integration is designed to solve. By connecting Slack with Okta, teams can centralize authentication, automate user provisioning and deprovisioning, and enforce consistent security policies across Slack.
What Is Slack-Okta Integration?
Slack–Okta integration connects Slack with Okta’s identity and access management platform to control how users authenticate and access Slack. It enables single sign-on (SSO) with Okta credentials, automates user provisioning and deprovisioning in Slack via SCIM, and enforces centralized security policies such as MFA and conditional access.
For IT and security teams, this integration reduces manual account management, minimizes the risk of orphaned Slack accounts, and ensures that only authorized users with verified identities can access Slack workspaces.
What Are the Benefits of Integrating Slack With Okta?
If you're managing identity and access for a growing team, integrating Slack–Okta integration goes beyond convenience. It helps standardize authentication through Slack Okta SSO, automate user lifecycle management, and reduce the operational overhead that comes with managing Slack at scale.
- Centralized Identity & Access Management: All Slack authentication and access policies are managed in Okta, allowing users to log in through Slack Okta SSO instead of separate credentials. This makes it easier for IT teams to enforce MFA, apply conditional access rules, and maintain consistent security controls across Slack.
- Real-Time Profile & Group Sync: With Slack Okta SCIM enabled, Slack user accounts are automatically created, updated, or deactivated based on changes in Okta. This removes manual account management and directly addresses user provisioning and deprovisioning in Slack, significantly reducing the risk of orphaned Slack accounts.
- Stronger Security & Compliance Posture: Using Slack SCIM provisioning, user attributes such as name, title, department, and group membership stay in sync between Okta and Slack. This ensures accurate directory information and predictable access to Slack workspaces without manual updates.
- Faster Onboarding & Offboarding Workflows: New hires gain access to Slack on day one through automated Slack provisioning, while departing employees are removed immediately when their Okta account is disabled — eliminating delays and security gaps in offboarding.
- Stronger Security and Compliance Posture: Combining Okta’s identity controls with Slack’s enterprise security features supports compliance efforts such as Slack HIPAA compliance and Slack Enterprise Grid compliance, while maintaining clear audit trails for authentication and access changes.
- Reduced IT Overhead & Help-Desk Tickets: By automating login and access controls through Slack access management integration, IT teams spend less time handling repetitive access requests and fewer tickets related to password resets or manual Slack user changes.
- Improved End-User Productivity: Fewer login roadblocks, consistent profiles across tools, and immediate access to the right Slack workspaces enable teams to collaborate without friction.
- Scalable Group-Based Access Control: Slack access can be assigned using Okta groups, making Slack Enterprise Grid SSO easier to manage for large, distributed teams. This approach is especially useful when evaluating Slack SCIM provisioning which plans support group-based access at scale.
- Unified Reporting & Audit Trails: Authentication events, provisioning actions, and access changes are logged centrally, helping admins review Slack SSO configuration, validate Slack SSO settings, and investigate issues using enterprise audit logs.
Which Okta Features Are Used in Slack Integration?
The Okta features used in Slack Okta integration mainly focus on secure authentication and automated user lifecycle management. In practice, you’re enabling two things:
- Slack Okta SSO so users can sign in with Okta credentials
- Slack Okta SCIM so user provisioning, profile sync, and deactivation happen automatically
Here are the key capabilities that power the integration.
Before diving into the setup process, there's a necessary prerequisite to consider: your Slack plan tier. Not all Slack plans support Okta integration.
Which Slack Plans Support Okta Integration and SCIM Provisioning?
Only Business+ and Enterprise Grid support Slack Okta SSO and Slack SCIM provisioning. Free and Pro plans do not include these capabilities, which makes them incompatible with full Okta-based identity automation.
This distinction matters because many teams assume SSO alone is enough, but without SCIM, user provisioning and deprovisioning in Slack still requires manual work.
Now that you've confirmed your Slack plan supports Okta integration, let's walk through the complete setup process.
How To Set Up Slack-Okta Integration for SSO, User Provisioning, and Deprovisioning?
This step-by-step guide walks you through setting up Slack–Okta integration using SAML and SCIM. Once complete, users will authenticate through Slack Okta SSO, and Slack accounts will be automatically created, updated, or deactivated using Slack SCIM provisioning.
Before you begin, make sure:
- You’re on a Slack Business+ or Enterprise Grid plan
- You have Org Admin access in Slack
You have Admin access in Okta
Step 1: Add the Slack App in Okta
This step connects Slack to Okta so authentication and provisioning can be managed centrally.
- First, log in to your Okta Admin dashboard. It will direct you to the authentication screen, where you will be prompted to enter a six-digit code using the Okta Verify mobile app. Once verified, you will be able to see the screen below:
- In the left-hand menu, go to Applications > Applications, then click Browse App Catalog.
- Search for Slack, and select the official Slack SCIM app—not the legacy SAML-only version.
- Click Add.
- Next, set your Application Label (e.g., “Slack – Enterprise Grid”). If you’d prefer this app to remain visible only to admins, check the box for 'Do not display application icon to users'.
- Then, click Done to complete the app addition.
Step 2: Enable API Integration in Okta
To support Slack SCIM provisioning, Okta needs permission to communicate with Slack’s SCIM API.
- Once the Slack app is added and users are assigned, you’ll need to enable API integration so that Okta can communicate with Slack.
- From the Slack app page in Okta, click the Provisioning tab at the top.
- In the left-hand menu, click Integration.
- Select the box labeled 'Enable API Integration'.
- Now, open a new browser tab and log in to Slack as an Org Admin. You’ll need admin-level permissions to authorize the connection between Okta and Slack.
Step 3: Generate the SCIM Token in Slack
This step connects Slack to Okta so authentication and provisioning can be managed centrally.
- Next, you’ll need to grab an SCIM token from Slack so Okta can securely manage users.
- Start by navigating to admin.slack.com.
- In the left-hand menu, go to Security > Authentication > Provisioning.
- Click Create Token. You may be asked to re-authenticate.
- Slack will generate a long SCIM token (it starts with xoxp-).
Important: Copy this token and store it somewhere safe. It acts like a password, granting full access to manage users via SCIM. You’ll use this token back in Okta to complete the connection.
Step 4: Authenticate the SCIM API in Okta
- Head back to Okta.
- In the API Integration section of the Slack app settings, paste the SCIM token you copied earlier into the API Token field.
- Click Test API Credentials to confirm the connection.
- If everything works, you’ll see a green check mark.
- If it fails, double-check that:
- Your Slack plan supports SCIM (Enterprise Grid is required)
- You’re signed in as a Slack Org Admin
Once you see the green check, click Save to continue.
Step 5: Set Up Provisioning Features
Now that your SCIM token is connected, it’s time to enable provisioning features (which allow Okta to create, update, and remove Slack users automatically).
1. Still in the Provisioning tab of the Slack app, click To App in the left sidebar.
2. Then, click Edit, and enable the following options:
- Create Users
- Update User Attributes
- Deactivate Users
- Push Groups (optional but recommended)
- Reactivate Users (optional)
- Import Schema Discovery (optional)
3. Click Save to confirm your changes.
What This Setup Gives You
After completing these steps:
- Users sign in using Slack Okta SSO
- Slack accounts are created and removed automatically
- Profile and group changes stay in sync
- Manual Slack access management is largely eliminated
At this point, most teams have identity automation in place — but day-to-day access requests and operational workflows still happen inside Slack. That’s where additional tooling often becomes necessary.
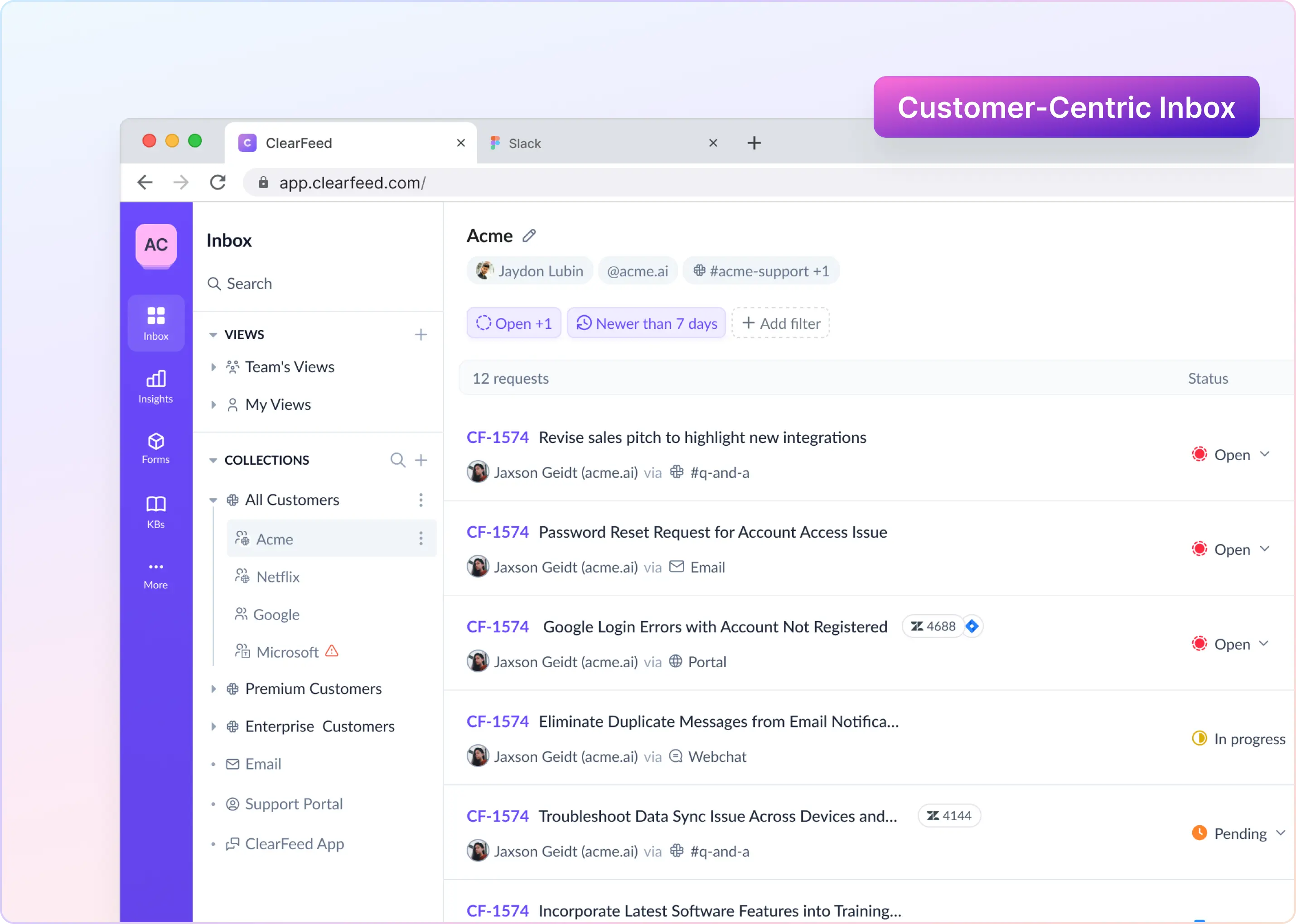
How ClearFeed Completes Your Slack-Okta Integration
The native Slack–Okta integration does an excellent job of handling authentication and automated user provisioning and deprovisioning in Slack. Okta becomes your source of truth for identity, and Slack access stays tightly controlled.
But for most IT teams, identity management is only part of the job. Once users are inside Slack, IT, HR, and Ops teams still deal with:
- Access requests coming in Slack channels and DMs
- App permission changes that require approvals
- Urgent issues that need context, ownership, and follow-up
These workflows don’t flow through Slack Okta SSO or Slack SCIM provisioning. They happen in Slack, in real time and that’s where teams often lose visibility and control.
As this comparison shows, both solutions serve different but complementary purposes. Okta is your source of truth, and the native Slack-Okta integration is ideal for managing user provisioning directly within Slack. Slack is where your users are. ClearFeed provides users in Slack a comprehensive way to manage users, groups, and app access in Okta - in an easy but secure manner. Try our free trial for 14 days or book a demo to learn more about Slack-Okta integration.